- Set up and stabilize the Windows 2000 SP1–based server that will be used as the certificate server.
- Install the High Encryption Pack.
- Locate the installation CD and ensure that share point is ready.
- On the Start menu, point to Settings.
- Click Control Panel.
- Double click Add/Remove Programs.
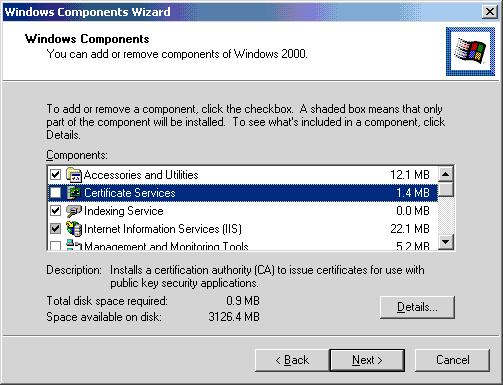
- Click Certificate Services from the Components list.
- Click Next.
- When prompted, click Yes to continue.

- Select the Stand-alone root CA button.
- Check the Advanced options check box.
- Click Next.
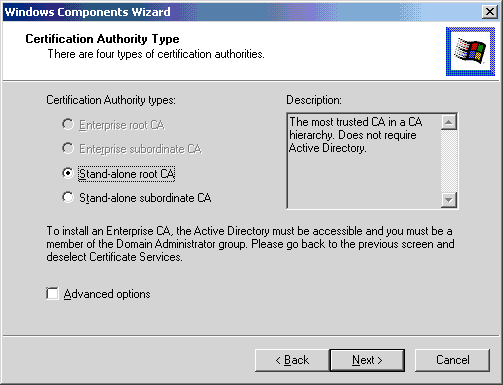
- Select Microsoft Enhanced Cryptographic Provider v1.0 from the CSP list.
- Select SHA-1 as the hash algorithm.
- In the
Key lengthbox, increase the number from the default of1024to 4096. - Click Next.
With the High Encryption Pack installed, the additional cryptographic service provider (CSP) option exists.
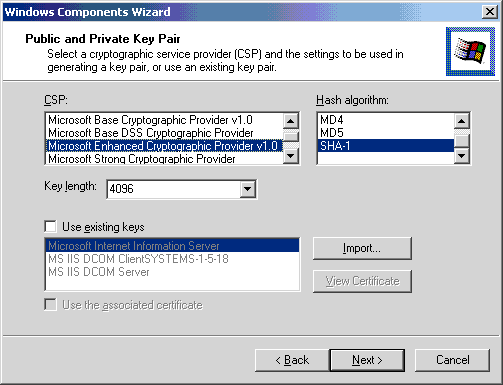
In this step the identity of the certifying authority and its lifespan are configured.
In configuring the identity of the certifying authority one must plan this in advance because this name cannot be changed. The identity should be considered to be permanent.
Configure the certifying authority accordingly, and ensure that the electronic mail address is not likely to change during the declared service life.
The declared value of the lifespan affects the serviceability of the certificate server. This is because the root CA can only issue certificates that have a lifespan less than the root, which is true for the entire hierarchy, if implemented. Therefore, if the root CA is configured with a ten year lifespan, and the subordinate certifying authorities are configured with a five year lifespan, the users can employ the certificate services for less than five years. If the PKI deployment takes two years to fully deploy, users have even less time to use the service.
Certifying authorities may be renewed and the lifespan subsequently changed, but this requires administration. Keep administration to a minimum to decrease the opportunity of service interruption due to human intervention or accident.
Decisions made by the deployment team are important. Aggregate security requirements must be known, declared, and put in writing before putting the service into live production.
- Type the appropriate information in the text boxes provided.
- Click Next.
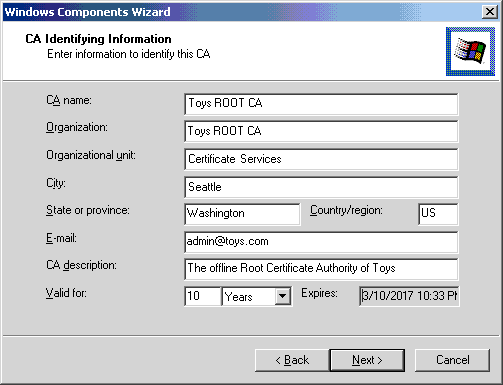
The certifying authority is being created. The root certificate is self signed by the root CA.
- Click Next when the process is finished.
Backup and restore of the CA is directed against the folder declared in the Shared folder box.
The wizard will proceed to the Data Storage Location.
- Enter the appropriate information in the Certificate database and Certificate database log boxes.
- Click Next.
Internet Information Services will be halted and restarted as the Windows Components Wizard proceeds.
- Click OK.
- Click OK complete the installation process.
The certifying authority can now issue certificates to users. Before proceeding, locations of the Certificate Revocation List (CRL) and Authority Information Access (AIA) need to be specified. Strong PKI applications verify these locations first to check the status of certificate revocation and public key download. These should be installed on the root CA computer, which will not be shut down because its uptime is considered a priority.
- Open the Microsoft Management Console (MMC) associated with the certifying authority.
The green check mark indicates that the service is running.
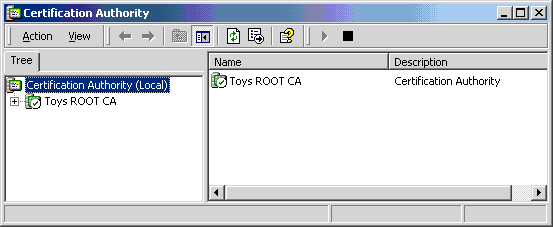
- Right click to obtain properties on the root CA.
- Click Policy Module/Configure/X.509 Extensions.
Because the root CA computer is essentially invisible to the network, the CRL and CRT files are manually copied to the Web server. The name of the Web server is used in this example. However, a DNS name is preferred for production because a change in the Web server computer name would break the PKI.
If the root CA server is also the CRL distribution point,
to have the location of the CRL distribution point in the self-signed
certificate for the root CA, create the root CA by using a Capolicy.inf file.
This is also necessary for setting a certification practice statement URL in the root CA
certificate. Capolicy.inf is placed in the \winnt directory,
and looks similar to the following code:
[Version]
Signature= "$Windows NT$"
[CAPolicy]
Policies = LegalPolicy, LimitedUsePolicy, ExtraPolicy, OIDPolicy
[LegalPolicy]
OID = 1.2.3.4.5.6.7.22.43
Notice = "Legal policy statement text."
[LimitedUsePolicy]
OID = 1.2.3.4.5.6.7.22.47
URL = "http://http.site.com/somewhere/default.asp"
URL = "ftp://ftp.site.com/somewhereelse/default.asp"
Notice = "Limited use policy statement text."
URL = "ldap://ldap.site.com/some where else again/default.asp"
[ExtraPolicy]
OID = 1.2.3.4.5.6.7.22.53
URL = http://extra.site.com/Extra Policy/default.asp
[oidpolicy]
OID = 1.2.3.4.5.6.7.22.55
Publishing the root certificate to Active Directory is now ready. Once this step is complete, the path to the top of the certificate hierarchy msut be set.
System uptime from this point forward is crucial because the trust will be broken if the root CA cannot be accessed.
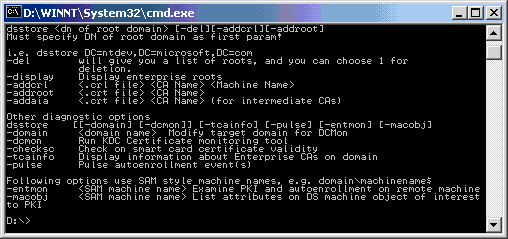
To publish, run Dsstore.exe from the Windows 2000 Server Resource Kit.
The following command line is used.
dsstore.exe DC=toys,DC=com –addroot ROOTCA.CRT "Toys ROOT CA"
Note that the variable identifiers are in uppercase.
During full deployment, replication must be complete before the certificate is available across the entire domain. The DSSTORE –pulse switch can accelerate this process.
Root authorities differ from subordinate authorities in that subordinates store CRL and Authority Information Access in Active Directory, which enables a Lightweight Directory Access Protocol (LDAP) query.
The process of installing a subordinate CA is similar to installing the root, and is identical for every subordinate to be created. Online authorities will use the offline root to sign the certificates they make available to the enterprise.
- Using the subordinate CA computer, sign in as an enterprise level administrator.
- On the Start menu, point to Settings, and then click Control Panel.
- Double click Add-Remove Programs
- Click to select the Windows Components sequence.
- Click on Add/Remove.
- Select the option to Install Certificate Services.
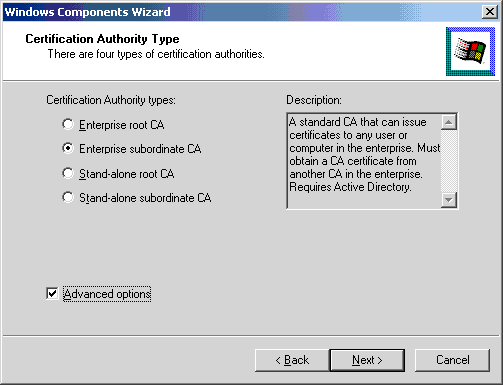
- Click Enterprise subordinate CA.
- Check the Advanced options check box.
- Click Next.
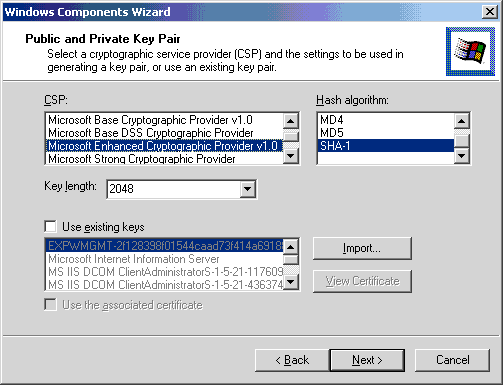
- In the CSP list, click Microsoft Enhanced Cryptographic Provider v1.0.
- In the Hash algorithm list, click SHA-1.
- In the Key length list, increase the number to 2048.
- Click Next.
Again, the identification should be planned in advance. The lifespan is determined by the root authority, and is one year by default. The certificates can be renewed. The one year default might be appropriate for a high security requirement. If this is not the case, the default lifespan can be modified by changing the following registry value on the root CA computer.
HKLM\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\name of
the root CA\ValidityPeriod
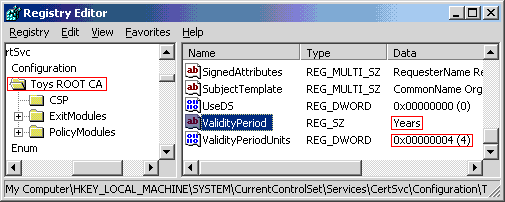
After the registry value has been changed, cycle the certificate service.
- Confirm the CA identifying information, and then click Next.
The wizard will proceed to the Data Storage Location.
There is an option to store configuration information in a shared folder. If this option is exercised, the specific computer should also have a maximum uptime goal.
- Enter the appropriate information in the Certificate database and Certificate database log boxes.
- Click Next.
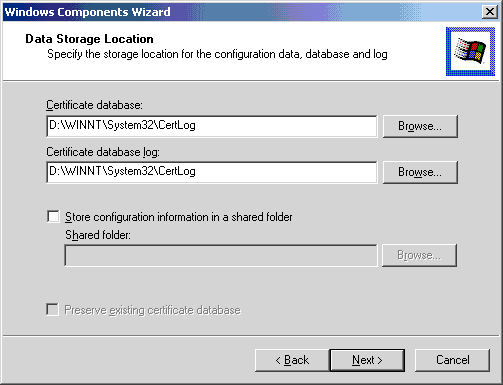
There are two options to have the subordinate certificate signed by the root. One is to send the request directly to the root. The other is to create a file for the root to process. For this exercise, create a file for the root to process because the root CA is not available on the network.
- Click Save the request to a file.
- Click Next.
- Follow the on-screen instructions to complete the installation process.
- Click OK.
The wizard will then state that the installation process is complete and that the service will be available when the certificate is processed and installed.
The Completing the Windows Components Wizard page appears.
- Click Finish to close the wizard.
To get the subordinate certificate request signed by the root, one can access the root computer directly by using the following procedure:
- Start the browser.
- On the Tools menu, click Internet Options to open the Internet Options dialog box.
- Click the Security tab.
- Click Trusted Sites.
- Click Sites.
- Clear the Require server verification check box.
- In the Add this Web site to the zone text box, type http://localhost/.
- Click Add.
- Click OK.
- Set the appropriate security level to a custom level, or accept the default level.
- Click Apply.
- Then click OK to close the Internet Options dialog box.
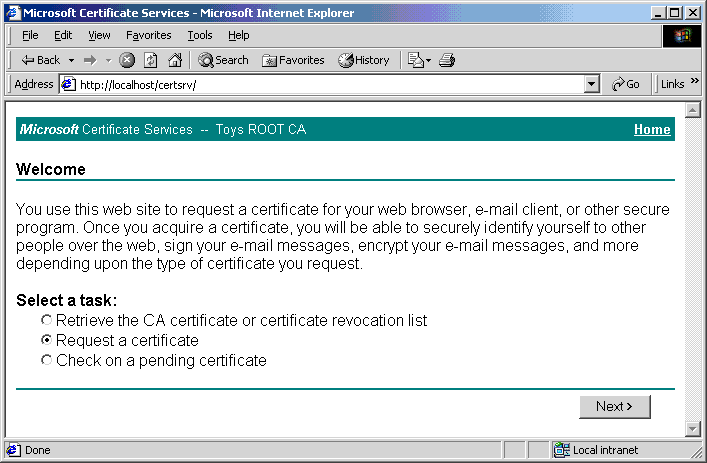
- In the browser's location box enter http://localhost/certsrv.
- Click Request a certificate radio button from the
Select a tasklist. - Click Next.
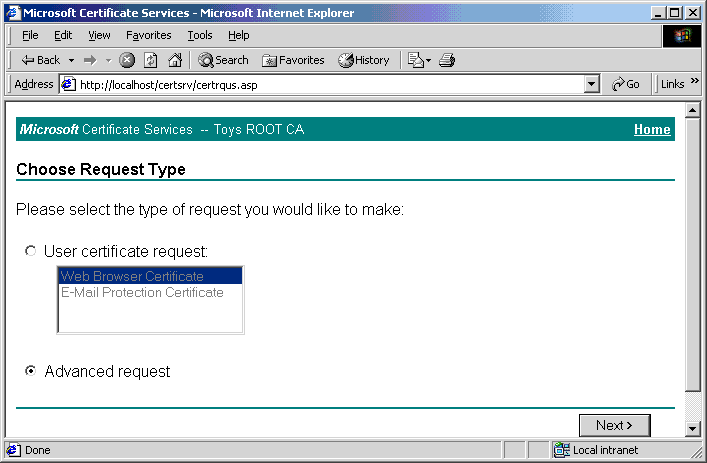
- Click on the Advanced request radio button.
- Click Next.
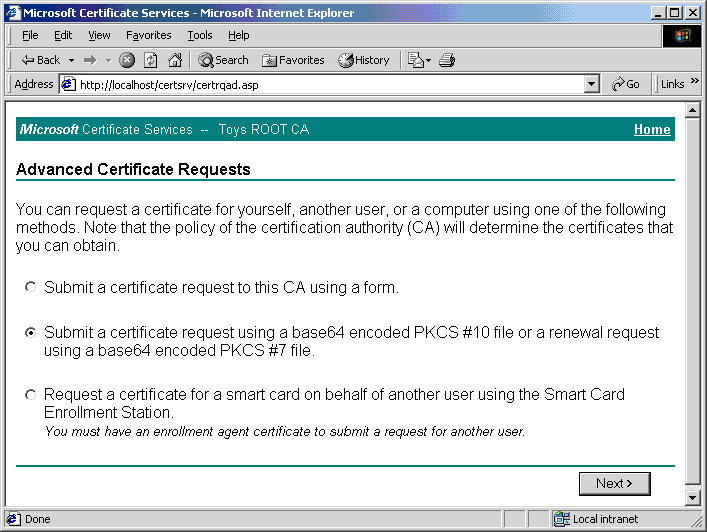
- Click Submit a certificate request using a base64 encoded PKCS #10 file or a renewal request using a base64 encoded PKCS #7 file.
- Click Next.
Base 64 files are encoded, not encrypted. Although base 64 files provide a foundation for encryption, base 64 encoders and decoders are readily available.
The following message will appear.
- Click OK to proceed.
- If the using a form button is selected then paste the base 64 encoded text into the form.
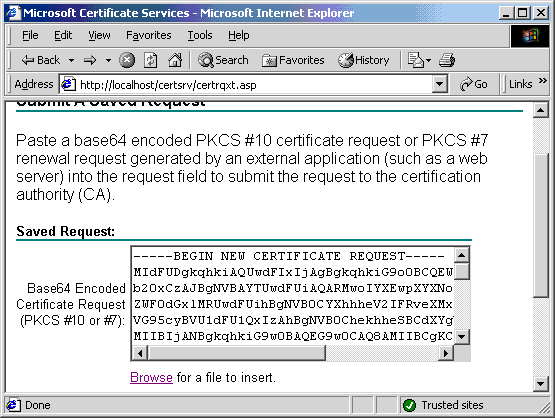
- Submit the request.
- Open the Pending Requests folder for the root MMC.
- Observe the pending request.
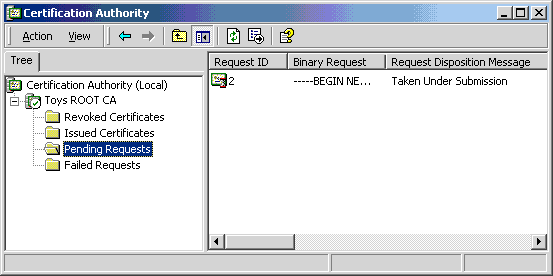
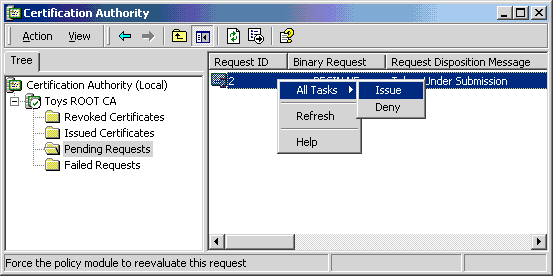
- Right click on Pending Requests.
- Select All Tasks.
- Click Issue.
An administrator can issue or deny the pending request. In a live production environment, always run the request against a registration authority to guarantee the authenticity of the request.
- Return to the browser.
- In the browser's location box enter http://localhost/certsrv.
- Click Check on a pending certifcate radio button from the
Select a tasklist. - Click Next.
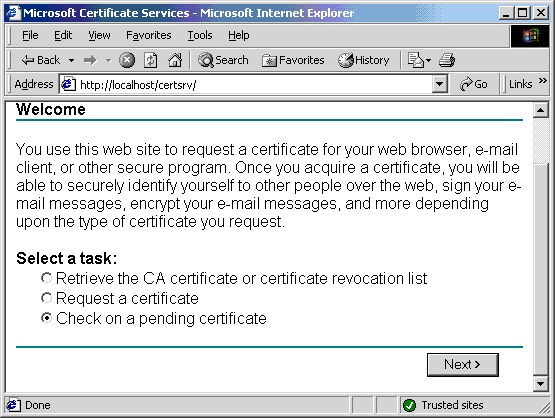
- Select a request to review.
- Click Next.
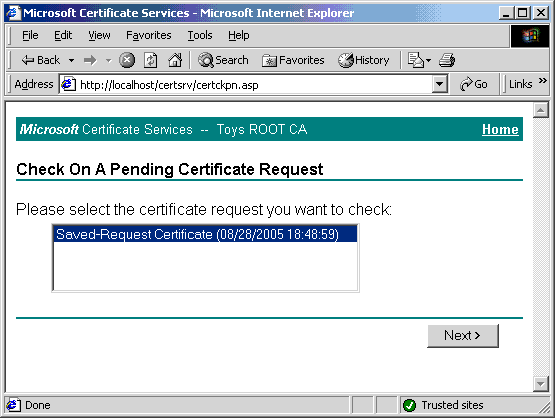
The certificate is issued, and it can be retrieved from a downloadable certification path and copied to a floppy disk. In a live production setting, the floppy disk can be hand-delivered to remote sites as needed.
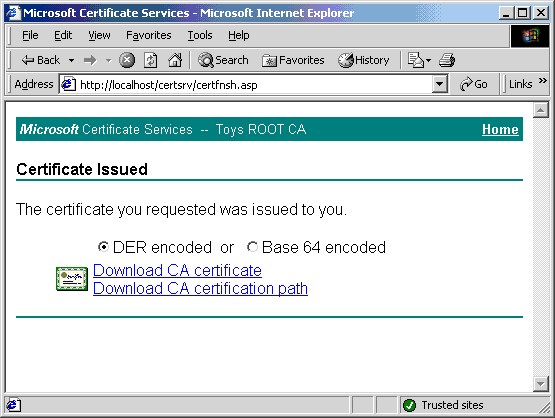
- Click on Toys WEST SUB CA under the Certification Authority (Local) folder.
- Open the MMC.
- Notice the red dot, which symbolizes that the service is not running or is completed.
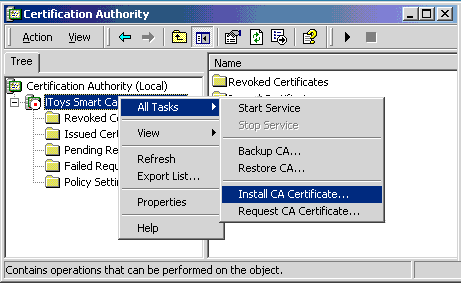
- Right click on Toys WEST SUB CA.
- Select All Tasks.
- Click Install CA Certificate.
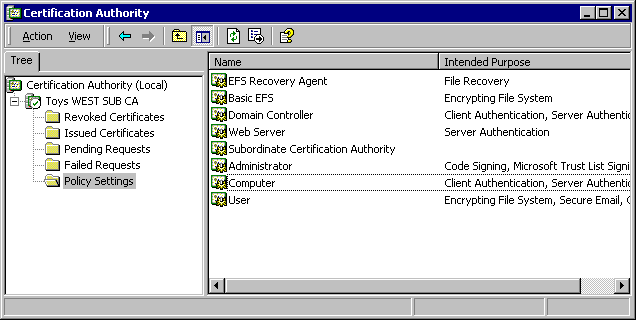
- Click on the Policy Settings folder.
- Click on Computer.
- Now view the subordinate CA in the Policy Settings folder.
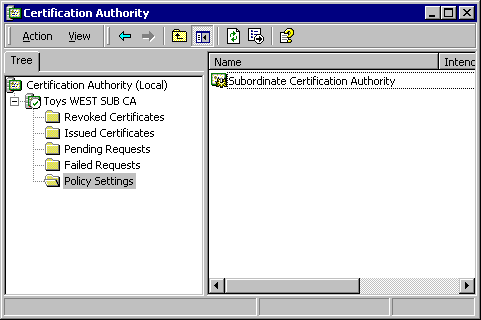
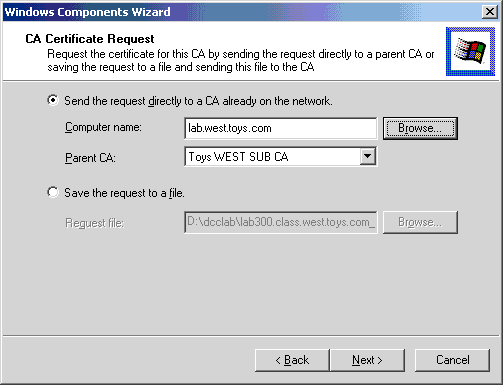
From this point forward, one can add subordinate CAs under the subordinate of the root. The installation process is identical to installations covered thus far. The process is simplified because one can sign certificates from the online certifying authority.
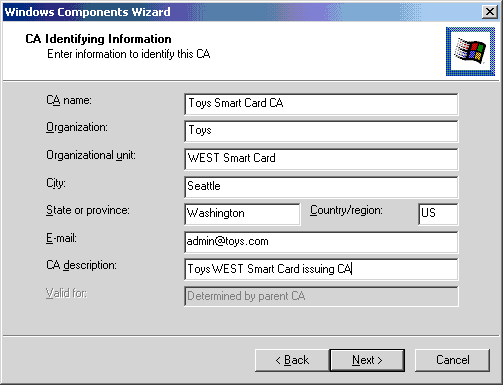
- Create a subordinate CA under the root's subordinate CA, by typing the appropriate information on the CA Identifying Information page.
- Click on the Send the request directly to a CA already on the network button to send the request directly to the root's subordinate CA.
- Click Next to finish the process.
It is vitally important to keep the online CA running at all times and serviced only by trusted operations personnel. Although file, print, and Web servers and services are often subject to change, the same should not be true for the certificate server is down the certificate hierarchy is compromised. Advanced preparation tasks will reduce this risk to a minimum.
Congratulations! You have successfully to set up a certificate hierarchy!